03 Dec What is data security and integrity?
If there’s anything we can assume when it comes to cybersecurity in the coming years, it’s that threats will not slow down.
Just hours after the hotly anticipated launch of new streaming service Disney+, thousands of hacked accounts were posted to black market forums.
In this particular instance, it seems that the users were locked out of their accounts due to hackers who tested for reused passwords that had already been compromised from another location, or perhaps from keylogging software. Still, this demonstrates that the appetite for valuable data is not slowing down.
Though it’s a less glamorous topic than data security, data integrity is just as essential to a functioning digital ecosystem.
Let’s take a look at what data security and integrity are, why they’re important and what we can do to properly maintain both.
A closer look: Data integrity
Data integrity refers to the overall consistency and usability of data so that it can be accurately and completely searched, retrieved and updated at all times. If proper data integrity standards are not maintained, data can become corrupted, making individual files inaccessible and unreadable, or producing larger errors that lead to system crashes.
Data integrity is closely related to security. Ineffective access control procedures can open the door to people who are not trained to properly handle sensitive data, or worse, it could expose that data to malicious actors who would seek to corrupt or steal it.
Proper data integrity is essential to reliable digital functioning because it allows data to be fully searched, traced, recovered and connected. As consumer and business computing needs have broadened the demand for increasingly large and complex data sets, data integrity has become more important and more complicated.
In order to safeguard data from being corrupted, integrity constraints are deployed.
Types of integrity constraints
Three standard types of integrity constraints protect data as it’s used in modern relational databases:
- Entity integrity refers to the fact that all tables in the database must have primary keys.
- Referential integrity relates to the use of foreign keys and ensures that tables are synced.
- Domain integrity describes the interaction of data with the overall domain.
A fourth type of integrity constraint describes nonstandard impositions set by the unique needs of the data’s user, whether that’s a private company, a government agency, or another type of organization.
User-defined integrity encompasses rules established by the user to suit their individual needs beyond the standard entity, referential and domain constraints.
In order to ensure they’re maintaining data integrity properly, many users, depending on their needs, could choose to implement audit trails logging alterations of data.
Overall, data integrity is a complicated and technical field that helps ensure data is accurate, accessible, searchable, retrievable, recoverable and consistent. It helps protect against outright data loss. Because of its highly technical nature, it’s important that access control is properly limited to only allow access by qualified individuals. Those individuals must be properly trained to reduce human error and audit trails should be put in place to troubleshoot corruption if it occurs.
Change control processes, which help establish continuity and consistency as data is managed and modified, are essential as well.
A closer look: Data security
Data security is the systematic strategy of safeguarding and protecting data against numerous vulnerabilities. Sensitive data can be a target for profit-motivated and ideologically driven individuals as well as digital vandals. Sometimes your data is a target in and of itself. Other times, you’re the real target, and restricting access to your data, or corrupting it, will hurt you and you and damage your operations
In order to establish the importance of this field, it’s sometimes referred to as information security, highlighting the fact that what’s at risk is more than raw data. What’s at stake is really complicated information, and the protection of that information can be vital for organizations.
In order to draw a distinction from data integrity, we should note that data security is primarily concerned with protecting data from outside intrusions. While breaches can lead to ransomware and other attacks that jeopardize the integrity of the data, other security failures can result in exfiltration or spying that doesn’t meaningfully impact the integrity of the existing data.
Why is data security important?
The answer to this question will vary depending on what kind of data you have access to and what you store, but if you store any personal information for people within or outside your organization, then you have a responsibility to honor their wishes for data privacy and confidentiality.
Especially when data breaches are avoidable, the damage to your organization from a widely discussed incident can be incalculable.
In addition to safeguarding the information and communications of your employees, partners and clients or customers, data security is important because it defends your trade secrets and other sensitive internal knowledge.
Data security is also fundamentally important because, even for material that isn’t particularly private, experiencing restrictions to routinely needed data can grind your operation to a halt in no time.
How do you manage data security and privacy?
There are numerous security measures you can take to lock down data and ensure the privacy of stored information from your users.
From deploying industry-standard encryption best practices for sensitive data to protecting databases with restricted access and improved physical security protocols, as well as regularly searching for, and patching, vulnerabilities, managing data security and privacy is not a one-time action. It’s an ongoing effort of continuous improvement.
In addition, here are few guidelines to keep at the forefront of your data security strategies if you handle sensitive or private information:
- Don’t take more personal information that you need.
- Only keep personal information on file for as long as you need it.
- Delete personal information once it’s no longer needed.
- Physically destroy and render unreadable hard drives and other data storage devices when you dispose of them.
Lastly, make sure that all of your technology vendors and partners have responsible security protocols in place for handling sensitive data and strong data security protocols.
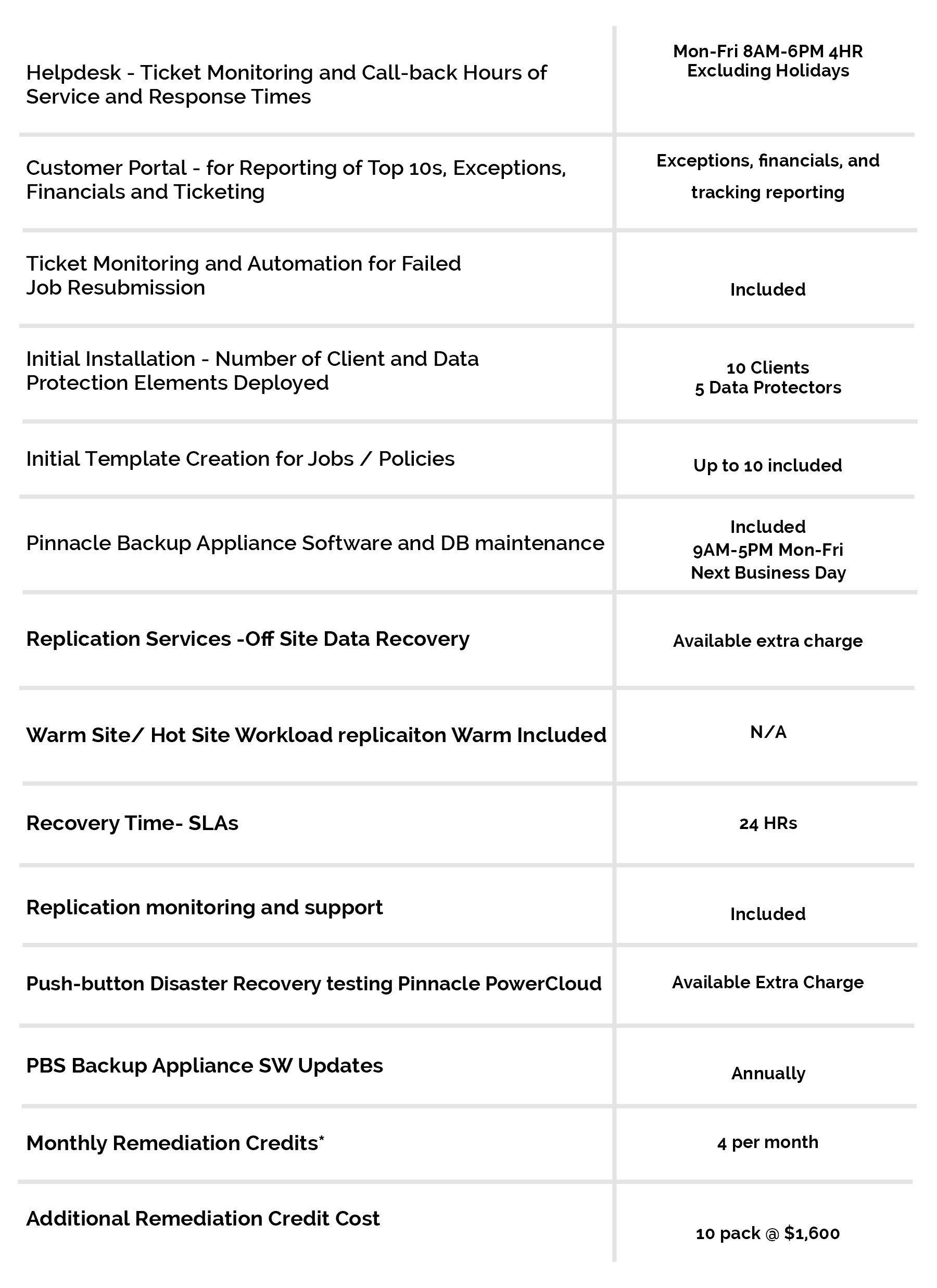
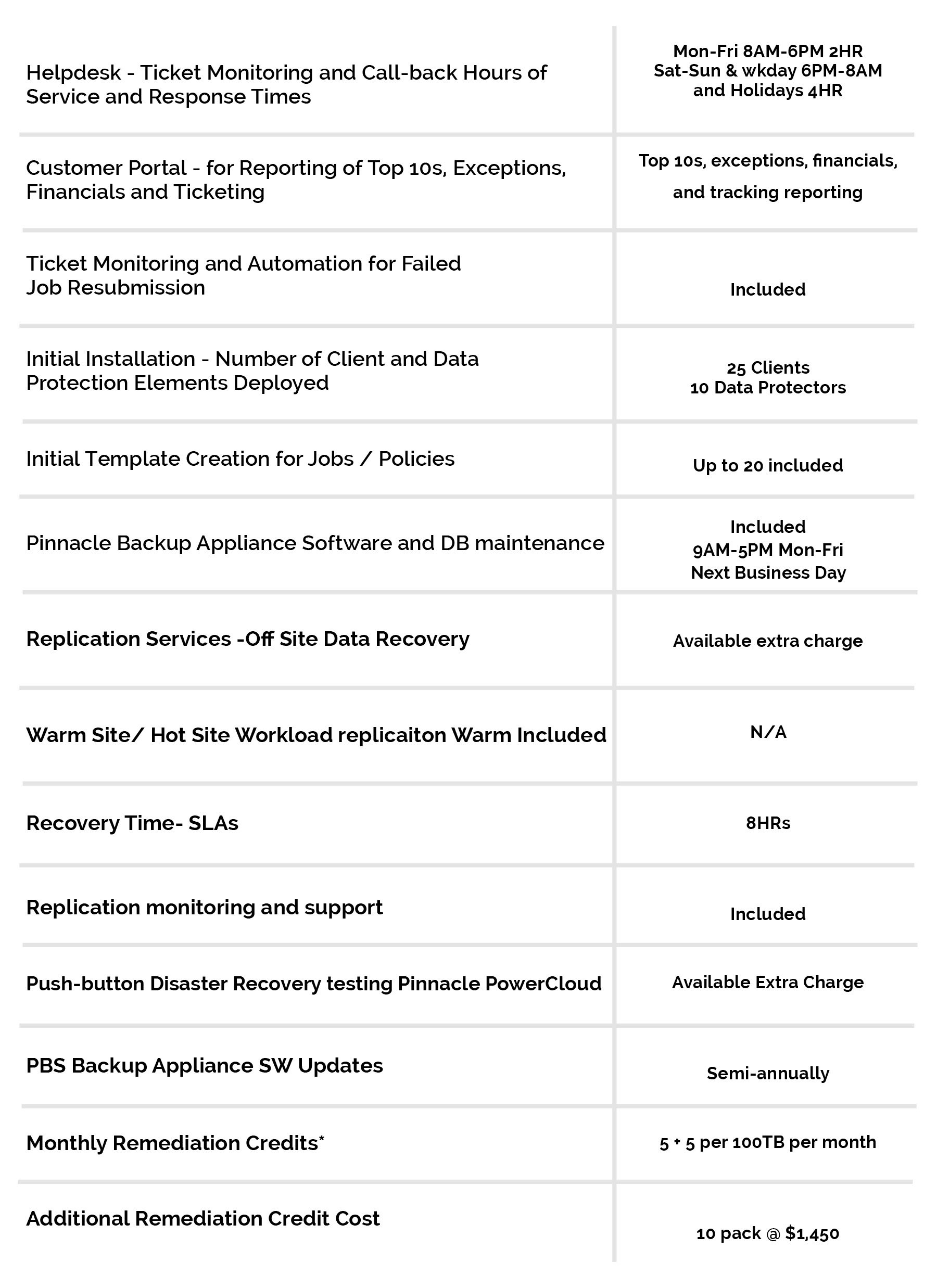
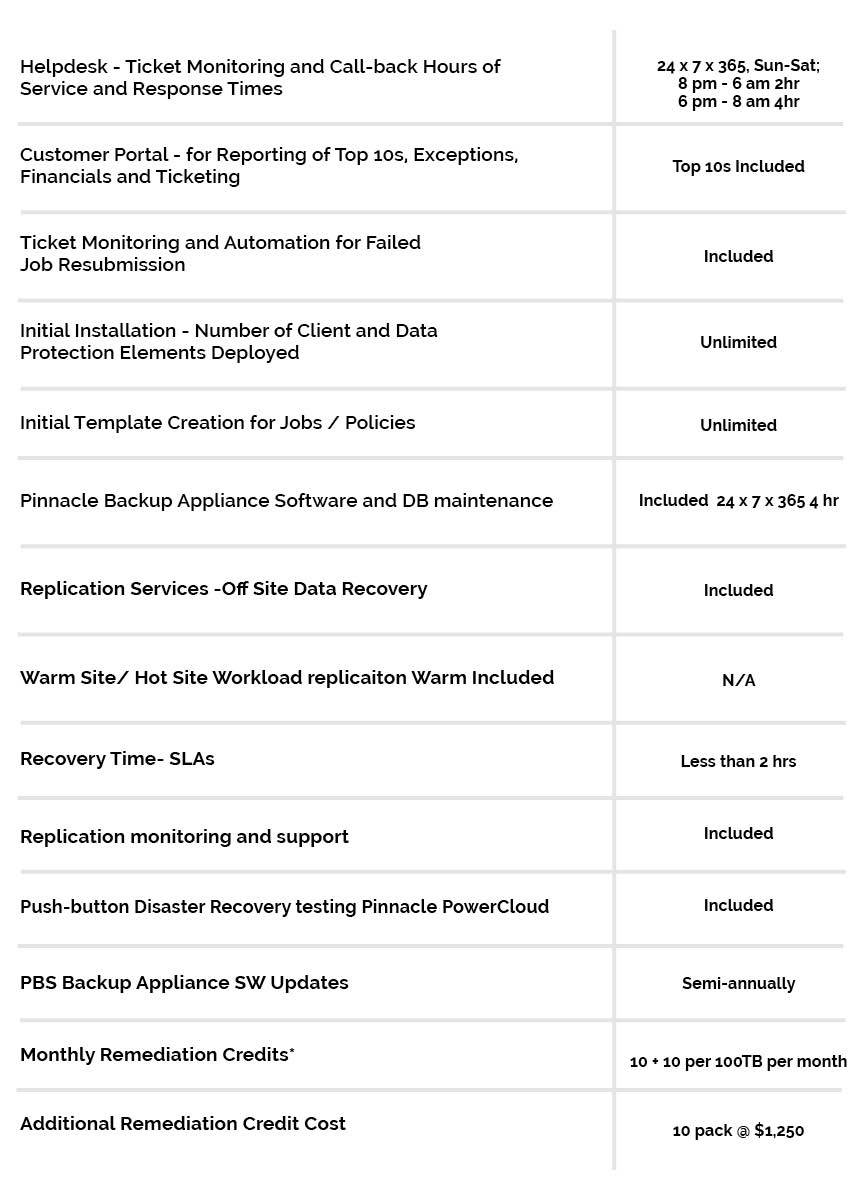
Learn more about Pinnacle’s information security solutions today. We’re here to help guard the integrity and security of your data.